We spotted a new variant of the documents used in the cyber attacks against Uyghur back in February.
This variant was first submitted to VirusTotal on April 11 from China. This time it uses IUHRDF, which may be a reference to International Uyghur Human Rights & Democracy Foundation, instead of Captain as the author:

The payload is still the same besides using different filenames and command and control server.
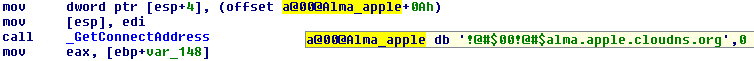
It uses “alma.apple.cloudns.org” as the command and control server:
It creates the following copy of itself and launch point:
~/Library/Application Support/.realPlayerUpdate
~/library/launchagents/realPlayerUpdate.plist
Or it may create the following instead (when executed with 2 parameters):
/Library/Application Support/.realPlayerUpdate
/library/LaunchDaemons/realPlayerUpdate.plist
It remains pretty much the same malware and is generically detected as Backdoor:OSX/CallMe.A since February.
MD5: ee84c5d626bf8450782f24fd7d2f3ae6 – poadasjkdasuodrr.doc
MD5: 544539ea546e88ff462814ba96afef1a – .realPlayerUpdate
Leave a reply



