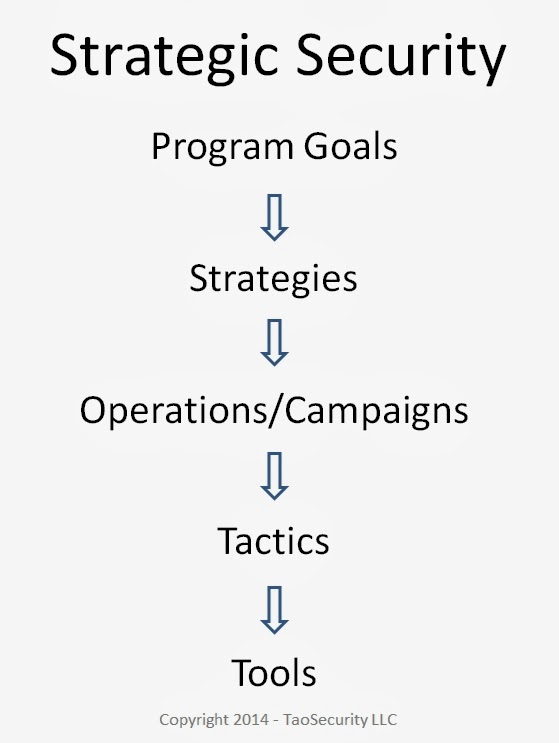
#attribution is the hottest word in #digital security. The term refers to identifying responsibility for an incident. What does it matter, though? Here are five reasons, derived from the five levels of strategic thought. I’ve covered those before, namely in The Limits of Tool- and Tactics-Centric Thinking.
Note that the reasons I outline here are not the same as performing attribution based on these characteristics. Rather, I’m explaining how attribution can assist responsible actors, from defenders through policymakers.
1. Starting from the bottom, at the #tools level, attribution matters because identifying an adversary may tell defenders what software they can expect to encounter during an intrusion or campaign. It’s helpful to know if the adversary uses simple tools that traditional defenses can counter, or if they can write custom code and exploits to evade most any programmatic countermeasures.
Vendors and software engineers tend to focus on this level because they may need to code different defenses based on attacker tools.
2. The benefits of attribution are similar at the Tactics level. Tactics describes how an adversary acts within an engagement or “battle.” It describes how the foe might use tools or techniques to accomplish a goal within an individual encounter.
For example, some intruders may abandon a system as soon as they detect the presence of an administrator or the pushback of a security team. Others might react differently by proliferating elsewhere, or fighting for control of a compromised asset.
Security and incident response teams tend to focus on this level because they have direct contact with the adversary on a daily basis. They must make defensive choices and prioritize security personnel attention in order to win engagements.
3. The level of Operations or Campaigns describes activities over long periods of time, from days to months, and perhaps years, over a wider theater of operations, from a department or network segment to an entire organization’s environment.
Defenders who can perform attribution will better know their foe’s longer-term patterns of behavior. Does the adversary prefer to conduct operations around holidays, or certain hours of the day or days of the week? Do they pause between tactical engagements, and for how long? Do they vary intrusion methods? Attribution helps defenders answer these and related questions, perhaps avoiding intrusion fatigue.
CISOs should focus on this level and some advanced IR teams incorporate this tier into their work. This is also the level where outside law enforcement and intelligence teams organize their thinking, using terms like “intrusion sets.” All of these groups are trying to cope with long-term engagement with the adversary, and must balance hiring, organization, training, and other factors over budget and business cycles.
4. At the level of #strategy, attribution matters to an organization’s management and leadership, as well as policymakers. These individuals must decide if they should adjust how they conduct business, based on who is attacking and damaging them. Although they might direct technical responses, they are more likely to utilize other business methods to deal with problems. For example, strategic decisions could involve legal maneuvering, acquiring or invoking insurance, starting or stopping business lines, public relations, hiring and firing, partnerships and alliances, lobbying, and other moves.
Strategy is different from planning, because strategy is a dynamic discipline derived from recognizing the interplay with intelligent, adaptive foes. One cannot think strategically without recognizing and understanding the adversary.
5. Finally, the level of #policy, or “program goals” in the diagram, is the supreme goal of government officials and top organizational management, such as CEOs and their corporate boards. These individuals generally do not fixate on technical solutions. Policymakers can apply many government tools to problems, such as law enforcement, legislation, diplomacy, sanctions, and so forth. All of these require attribution. Policymakers may choose to fund programs to reduce vulnerabilities, which in some sense is an “attribution free” approach. However, addressing the threat in a comprehensive manner demands knowing the threat. Attribution is key to any policy decision where one expects other parties to act or react to one’s own moves.
Remember the five levels of strategic thought and their associated parties and responsibilities when you hear anyone (especially a techie) claim “attribution doesn’t matter” or “don’t do attribution.”
Also, check out Attributing Cyber Attacks by my KCL professor Thomas Rid, and fellow PhD student Ben Buchanan.
Tweet
Leave a reply