Harry Delaire
Data Optimization AdvocateIn an era where digital connectivity underpins nearly every aspect of daily life, the threat of cyberattacks looms larger than ever, with California facing an increasing number of data breaches and phishing scams that jeopardize personal and public safety. From malware disrupting critical infrastructure to social engineering tactics targeting
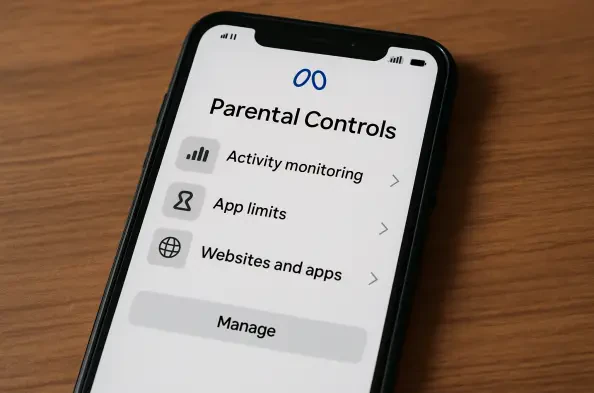
Setting the Stage for Teen Safety in a Digital Age In an era where social media platforms shape much of teenage interaction, a staggering statistic reveals that over 60% of teens encounter inappropriate content online, often through unchecked AI interactions. Meta, the powerhouse behind Instagram and Facebook, has rolled out new parental control
In a digital era where data serves as both currency and weapon, a chilling breach has shaken the very foundations of national security, exposing critical vulnerabilities in the systems meant to protect us. A hacker collective known as "the Com" has publicly released the personal details of hundreds of US federal officials from agencies such as the
Imagine navigating the internet, believing your activities remain private, only to discover that every click and every page load quietly assembles a digital portrait of you without your knowledge or permission. This isn’t the plot of a futuristic thriller but the reality of browser fingerprinting, a subtle yet powerful technique that websites and
Vernon Yai is a renowned data protection expert with a deep focus on privacy protection and data governance. As a thought leader in cybersecurity, Vernon has spent years developing cutting-edge techniques for risk management and safeguarding sensitive information. Today, we dive into a pressing issue shaking the cybersecurity world: a recent
In a striking display of defiance, over 30 major US news organizations have banded together to reject a newly introduced Pentagon press access policy, igniting a heated debate about the balance between national security and press freedom. Under the leadership of Defense Secretary Pete Hegseth, the policy imposes stringent rules on journalists