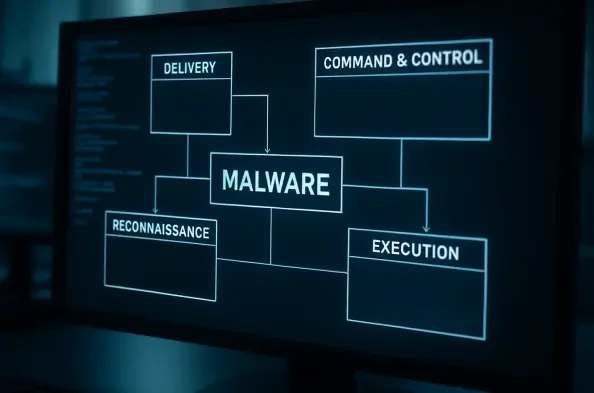
Endpoint Security
The silent infiltration of cloud-native infrastructure has entered a new phase of maturity where the distinction between professional security tools and malicious implants has effectively dissolved. Within this volatile landscape, the VoidLink malware framework has surfaced as a sophisticated, modular toolkit specifically engineered for
Vernon Yai is a preeminent figure in the landscape of data governance and hardware security, known for his deep technical expertise in protecting complex silicon architectures. With an illustrious career focused on risk management and the creation of advanced detection protocols, he provides critical oversight for companies navigating the
The digital foundation of modern computing experienced a significant reinforcement this month as chipmaking giants Intel and AMD released an unprecedented wave of security patches in a coordinated effort to address critical vulnerabilities. In a massive update for February 2026, the two companies collectively resolved over 80 security flaws
Chief Information Officers are navigating the most consequential technological shift of their careers, placing massive bets on AI platforms with the C-suite watching every move and the ground shifting beneath their feet. This high-stakes gamble has ignited a widespread AI governance crisis, where the relentless pursuit of return on investment is
With AI-driven cyberattacks poised to become a dominant threat, the cybersecurity industry is in a high-stakes race to innovate. Leading this charge is Vernon Yai, a data protection expert specializing in privacy and data governance. His focus on risk management and pioneering new detection techniques places him at the forefront of this evolution.