Norman Ainsworth
Change Management AdvisorThe silent, algorithmic hum of artificial intelligence now orchestrates both the most sophisticated cyberattacks and the most advanced defenses, fundamentally reshaping the very nature of digital conflict. This shift is not a distant forecast but a present-day reality, one where the speed, scale, and intelligence of digital threats have outpaced
The relentless hum of servers is often drowned out by the constant siren of security alerts, a sound that has become the defining rhythm of the modern Security Operations Center. For too many security teams, the daily reality is a draining cycle of firefighting, chasing down threats that have already breached the perimeter. This perpetually
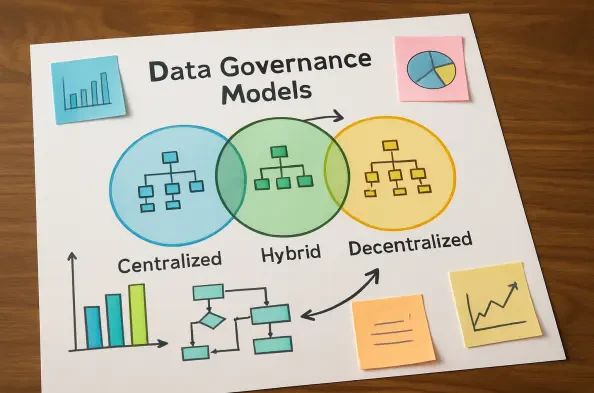
The paradox reverberating through corporate boardrooms is undeniable: while data has been crowned the undisputed king of the digital age, the very roles created to govern its kingdom are facing an unprecedented and alarming rate of dissolution. In a business environment more saturated with information than at any point in human history, the teams
For many Chief Information Officers, the term "data governance" has become synonymous with failed initiatives, bureaucratic roadblocks, and a deep-seated organizational resentment. This widespread aversion is not without cause, stemming from a history of flawed implementations where governance was either forcibly imposed from the top or siloed
The staggering financial and operational costs associated with flawed data have officially rendered traditional, manual handling methods obsolete in a world defined by massive, disparate information sources. Organizations are now compelled to adopt an intelligent, automated strategy to transform raw information from a liability into a strategic
The era of accepting an artificial intelligence vendor's assurances on data security and ethical practices at face value has decisively come to an end, fundamentally reshaping the procurement landscape for enterprise technology. As AI systems become deeply embedded in core business operations, the concept of "trustworthy AI" has evolved from an