Norman Ainsworth
Change Management AdvisorSetting the Stage for a New Market Dynamic Imagine a world where the fiercest tech giants, once locked in bitter rivalry, now join forces to reshape the very foundation of enterprise IT. In 2025, this is no longer a distant vision but a tangible reality in the cloud computing arena. Major players like Amazon Web Services (AWS), Google Cloud, and
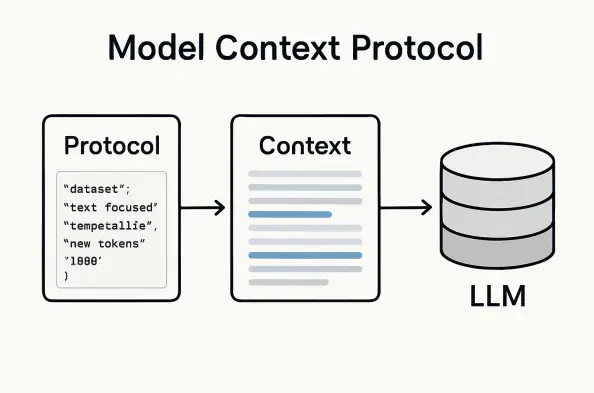
Imagine a world where connecting artificial intelligence assistants to vast arrays of external data and tools is as easy as plugging in a USB drive, yet the very simplicity that makes this possible also opens the door to a labyrinth of risks and roadblocks. This is the reality of Model Context Protocol (MCP) servers, a technology celebrated for
Imagine a world where the most precious resource isn’t gold or oil, but data—a digital treasure trove that holds the key to every decision, innovation, and strategy. In this realm, breaches and misuse loom like dark forces, threatening to unravel entire organizations. Who stands guard over this invaluable asset? Enter data stewards, the unsung
As data protection and privacy concerns continue to dominate the business technology landscape, few voices carry as much weight as Vernon Yai. A seasoned expert in data governance and risk management, Vernon has spent years crafting innovative strategies to detect and prevent breaches while safeguarding sensitive information. Today, we dive into
Vernon Yai has spent years at the forefront of data protection, carving out a reputation as a leading expert in privacy protection and data governance. With a sharp focus on risk management and pioneering detection and prevention techniques, Vernon brings a wealth of insight into how organizations can safeguard sensitive information in an
Setting the Stage for a Data Revolution In today's digital enterprise landscape, an overwhelming statistic looms large: nearly 90% of all information generated within organizations is unstructured, spanning emails, documents, multimedia files, and more. This vast, untamed data pool, lacking any predefined format, poses a monumental challenge for