For many Chief Information Officers, the term “data governance” has become synonymous with failed initiatives, bureaucratic roadblocks, and a deep-seated organizational resentment. This widespread aversion is not without cause, stemming from a history of flawed implementations where governance was either forcibly imposed from the top or siloed within an isolated IT department. Consequently, executives often perceive it as an expensive, overly complex tax on the business rather than what it truly is: an indispensable function for any modern enterprise. The critical challenge, therefore, is not to abandon governance but to fundamentally rethink the outdated, rigid models that have consistently failed to deliver on their promise.
Is “Data Governance” the Most Dreaded Phrase in Your Organization?
The negative reputation surrounding data governance is a direct result of past implementation strategies. Many organizations attempted a top-down mandate, forcing a universal framework onto diverse business units without their input or buy-in. This approach bred resentment and was often seen as an obstacle to agility, leading teams to create workarounds that undermined the entire initiative. The legacy of these command-and-control rollouts created a culture where governance is viewed as a burdensome constraint rather than a strategic enabler.
In other instances, the responsibility for governance was relegated solely to the IT department. This created an operational silo where a technical team, disconnected from the daily realities of the business, was expected to manage, secure, and ensure the quality of data it did not create or use. This isolation not only burdened IT but also guaranteed that the governance program would lack the business context necessary to succeed, further cementing its reputation as a purely technical and bureaucratic exercise.
Challenging this perception requires a shift in mindset from control to enablement. Effective governance is not a discretionary project but a core DataOps process that underpins reliable analytics, regulatory compliance, and confident decision-making. Viewing it as an indispensable business function, rather than an administrative tax, is the first step toward building a framework that adds demonstrable value and empowers users instead of restricting them.
The Core Conflict Why Traditional Governance Fails the Modern Data-Driven Enterprise
The fundamental flaw of traditional governance lies in its centralized, “command-and-control” structure. In this model, a central committee or a designated team effectively owns all enterprise data, dictating access policies and managing master data. While intended to create order, this approach inevitably becomes a bottleneck. Business teams seeking data for self-service analytics or innovative projects are forced to wait for approvals from a central body, stifling momentum and creating immense frustration.
This focus on restriction over enablement fosters a culture of data scarcity. Instead of empowering employees with the information they need, the centralized model inherently limits data access and discovery. This runs directly counter to the objectives of a modern, data-driven enterprise, which thrives on the democratization of data and the ability of teams to explore and innovate independently. The very mechanism designed to govern data ends up hindering its use and value.
The organizational cost of maintaining such a flawed system—or having no effective governance at all—is substantial. Poor governance directly harms business outcomes by leading to decisions based on untrustworthy data, creating compliance risks, and slowing down the organization’s ability to respond to market changes. The failure to evolve beyond outdated models is not just an operational inconvenience; it is a significant competitive disadvantage.
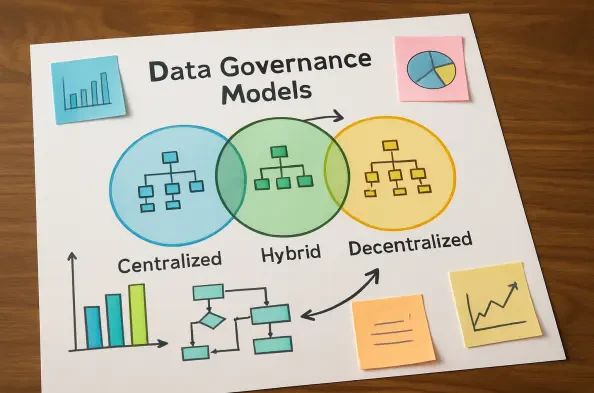
Exploring the Alternatives A Spectrum of Modern Governance Models
A truly modern alternative is the decentralized model, where governance responsibility shifts to the organizational edge. This approach empowers data producers and domain experts—the people who best understand the data’s context, quality, and use—to manage their own data flows and access controls. Philosophically aligned with contemporary concepts like the data mesh, this model promotes autonomy and accountability at the team level.
Occupying the middle ground is the federated model, which balances central oversight with distributed execution. In this hybrid structure, a lean central team sets enterprise-wide policies and standards, while dedicated governance resources are embedded within individual business units to handle implementation. This “lean and nimble” framework, as described by Mukul Sood, Chief Architect at Slalom, avoids the bottlenecks of a purely centralized system while ensuring cross-functional consistency.
For most organizations, the most practical path forward is a blended strategy that combines decentralized and federated elements. An initiative, such as improving data quality, could begin in a decentralized fashion within a single business domain. As that team develops best practices, its structure and learnings can be scaled and replicated across other departments, evolving into a federated model that supports broader data integration needs without imposing a rigid, top-down structure from the start.
The Business Case for Change Insights from Academia and Industry Leaders
The strategic value of moving away from centralized control is supported by significant academic research. Studies from institutions like Harvard Business School, Stanford, and MIT have demonstrated that decentralized firms are more resilient and perform better, particularly during periods of macroeconomic shock. The core finding is that in volatile environments, the value of local information and localized decision-making increases dramatically, providing a strong business case for empowering teams with greater data autonomy.
This empowerment is critical for navigating today’s complex business landscape. When teams closest to the customer or the operational challenge have the authority and the data to make timely decisions, the entire organization becomes more agile and responsive. Centralized bottlenecks are removed, allowing the enterprise to adapt more quickly to emerging threats and opportunities.
Industry leaders envision a future where this model becomes the norm. Mark Palmer of the Data Leadership Collaborative imagines a state where every “citizen” in the organization contributes to governance within their domain, supported by a federated structure that provides engineering and compliance expertise. This vision reframes governance from a restrictive function managed by a few to a collective responsibility that enhances data value for all.
Designing Your Blueprint A Practical Framework for Choosing the Right Model
To design an effective governance program, it is useful to map specific functions to the most appropriate model. The Data Governance Institute identifies six key focus areas that can serve as a guide. Domains such as Data Quality, Data Warehousing, and Business Intelligence, particularly when the data serves a specific function and is not a formal enterprise-wide “data product,” are well-suited for a decentralized approach. This allows teams to manage their analytical assets with the speed and context they require.
In contrast, functions that demand enterprise-wide consistency, such as Policy, Architecture, and overarching strategy, require a federated model from the outset. A central body, working in collaboration with business units, should define the core principles and standards to prevent duplicated efforts and ensure that individual systems can integrate into a cohesive whole. This approach provides a guiding framework without micromanaging execution.
The Special Case Why Data Security Governance Demands Centralization
Among all governance functions, data security—encompassing privacy, compliance, and security—demands a centralized or, at minimum, a strongly centralized component within a federated model. Enterprise data is not static; it flows constantly between corporate systems. For example, sensitive customer data may originate in a Salesforce automation tool, travel to a customer support platform, and ultimately reside in financial systems.
A fragmented, purely decentralized approach to managing privacy and compliance across this journey is untenable. It creates inevitable gaps and inconsistencies that expose the organization to significant regulatory risk and financial penalties. While governance can begin within individual domains for other functions, for security, an enterprise-wide perspective is essential from day one to ensure rules are applied consistently at every touchpoint.
Historically, the penalty for centralizing security was the immense manual effort required to manage access on a system-by-system basis. However, modern technology has largely removed this barrier. Advanced tools can now automatically discover sensitive data across the entire data estate and apply a single, unified policy to manage it without custom coding. This technological leap makes centralized security governance not only feasible but also a critical lever for mitigating risk effectively.
The era of monolithic, top-down data governance had conclusively failed, leaving a legacy of resentment and stalled progress. The path forward was not to abandon the principle of governance but to embrace a more nuanced strategy tailored to the realities of the modern enterprise. Successful organizations recognized the wisdom in decentralizing execution where local context was paramount and federating oversight where enterprise-wide consistency was key. For the non-negotiable domain of data security, they understood that a centralized policy framework, federated across the organization, was a foundational requirement for building trust and ensuring long-term resilience in an increasingly interconnected world.