Data Security
A recent comprehensive analysis by cybersecurity researchers has uncovered critical vulnerabilities within Model Context Protocol (MCP) servers, revealing how these essential AI components can be transformed into potent attack vectors for widespread system compromise. These specialized servers, which act as the crucial intermediaries that allow
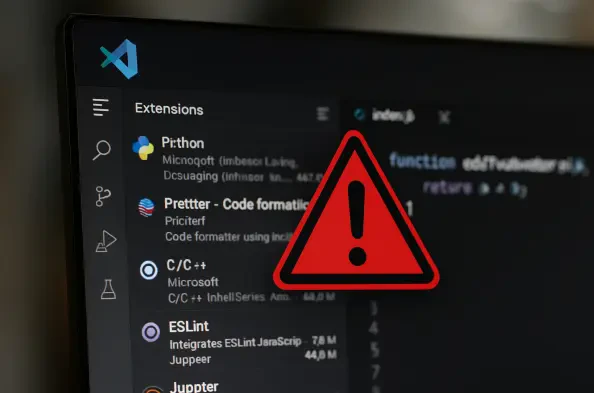
The very tools designed to streamline software development and enhance productivity have become a new battleground for cybercriminals, with the vast ecosystem of extensions for popular editors like Visual Studio Code emerging as a prime attack vector. A recent cybersecurity report has brought to light a targeted malware campaign that leverages the
The dawn of the quantum computing era presents a profound paradox, holding the promise of solving humanity's most complex challenges while simultaneously posing an existential threat to the foundations of modern digital security. The cryptographic standards that safeguard global finance, government communications, and personal data are
The ongoing battle between cybercriminals and security professionals has escalated dramatically with the emergence of a malicious tool engineered to dismantle digital defenses from the inside out. A sophisticated new threat, advertised on underground forums by the actor Crypt4You, operates not by hiding malware but by actively assassinating the
The digital asset industry is currently navigating a period defined by two monumental, non-speculative forces that will fundamentally shape its long-term trajectory, according to a recent comprehensive analysis from investment firm Grayscale. While daily market fluctuations often capture headlines, the more profound evolution is occurring on a