Data Security
As a leading expert in data protection and privacy governance, Vernon Yai has spent his career at the forefront of risk management, developing innovative techniques to safeguard our most sensitive information. In an era where AI platforms are built and deployed with breathtaking speed, often prioritizing growth over security, his insights have
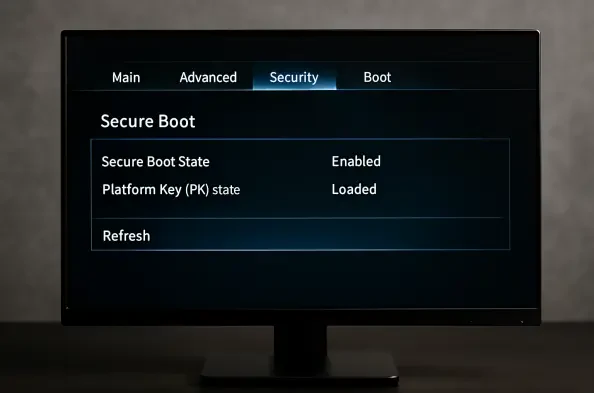
Deep within your computer's startup sequence, a fundamental security component is undergoing a mandatory evolution, a change that ensures the very foundation of your system's trust remains intact against emerging threats. This guide provides the necessary steps to verify your system's readiness for this critical update, ensuring its security and
The digital security that underpins global commerce and communication stands on the brink of a monumental shift, facing an unprecedented threat known as "Q-Day." This is the anticipated moment when a sufficiently powerful quantum computer will render today's most robust public-key encryption algorithms obsolete, exposing vast amounts of sensitive
A New Threat Emerges from the Shadows In the silent, digital battlegrounds of international espionage, a new weapon has surfaced that masterfully mimics legitimate software to avoid detection and steal sensitive information. This highly sophisticated malware, dubbed PDFSIDER, represents a significant evolution in cyber-espionage tooling, built
Tally Solutions, a cornerstone of business management software for nearly three million customers, found itself at a critical juncture as the global workforce dynamic shifted dramatically. The surging demand for secure, flexible, and remote access to its flagship TallyPrime platform presented an immense challenge, requiring an infrastructure that