Joshua Kaina
Secure Transfer ExpertIn an era where cyber threats are becoming increasingly sophisticated, organizations must stay ahead of the curve to protect their digital assets from relentless attacks, which are growing in both complexity and frequency. The realm of endpoint security and network monitoring is undergoing a seismic shift, fueled by groundbreaking technologies and
In a world where data security and scientific discovery increasingly depend on the smallest fractions of time, a groundbreaking experiment at CERN, the European Organization for Nuclear Research, is capturing global attention with its innovative approach. This initiative explores the fusion of high-precision timing technology with the mysterious
In a world increasingly reliant on secure data transmission, the quest for unbreakable communication systems has led scientists to the forefront of quantum technology, where a groundbreaking experiment at CERN, the European Organization for Nuclear Research, is capturing global attention. This pioneering work centers on White Rabbit, a timing
In an era where cyber threats lurk beyond the boundaries of traditional network defenses, organizations face an unprecedented challenge to protect their digital assets from external risks that can devastate reputations and bottom lines, making the need for advanced security measures more critical than ever. As phishing schemes, data leaks, and
I’m thrilled to sit down with Vernon Yai, a renowned data protection expert whose work in privacy protection and data governance has shaped industry standards. With a deep focus on risk management and cutting-edge techniques for safeguarding sensitive information, Vernon brings a wealth of insight to today’s discussion. We’ll be exploring the Wind
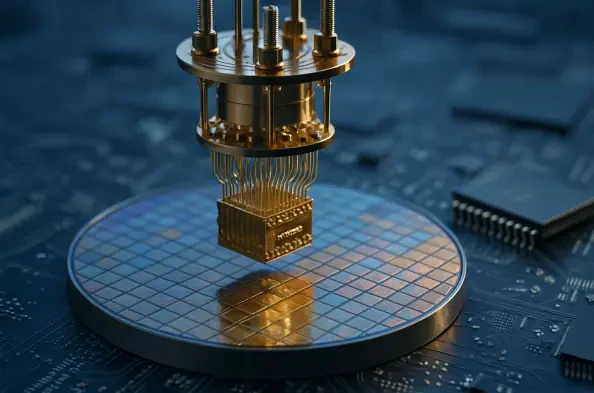
The convergence of quantum computing and semiconductor technology stands as a monumental leap forward, fundamentally altering the trajectory of computational power and artificial intelligence (AI) in ways that challenge the imagination. As of October 2025, this fusion is not merely a theoretical concept but a dynamic force driving innovation