Joshua Kaina
Secure Transfer ExpertThe silent arrival of automated shopping agents on e-commerce platforms represents less of a gentle evolution and more of a seismic shift, fundamentally altering the relationship between customer and retailer. As consumers begin delegating purchasing decisions to intelligent bots, retailers face a new, non-human clientele with an insatiable
The looming power of quantum computing presents a fundamental threat to the cryptographic foundations that secure the digital world, and the Ethereum Foundation is now formally escalating its defense with a comprehensive, multi-faceted strategy to future-proof the network. Building upon research that began in 2019, this initiative has been
A powerful consensus is forming within the highest levels of corporate leadership, framing artificial intelligence not merely as a supportive tool but as the future bedrock of enterprise, with a clear target set for its financial coming-of-age. While the immediate landscape is characterized by aggressive investment and considerable uncertainty,
The boardroom mandate for artificial intelligence has become an undeniable force, yet the promised returns often remain frustratingly distant, creating a widening chasm between executive ambition and tangible results. Against this backdrop of high expectations and sluggish progress, a landmark partnership between enterprise software leader
In an increasingly interconnected global economy, the seamless flow of data across borders has become a critical lubricant for trade and investment, yet it is often hampered by a web of compliance hurdles, security risks, and a fundamental lack of trust. Addressing this challenge head-on, Singapore and Shenzhen have initiated a landmark
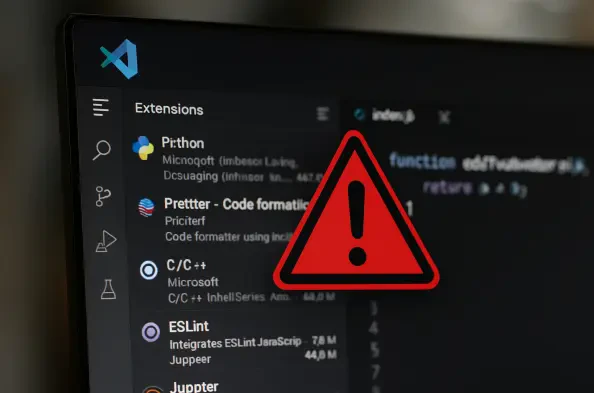
The very tools designed to streamline software development and enhance productivity have become a new battleground for cybercriminals, with the vast ecosystem of extensions for popular editors like Visual Studio Code emerging as a prime attack vector. A recent cybersecurity report has brought to light a targeted malware campaign that leverages the