Cloud Security
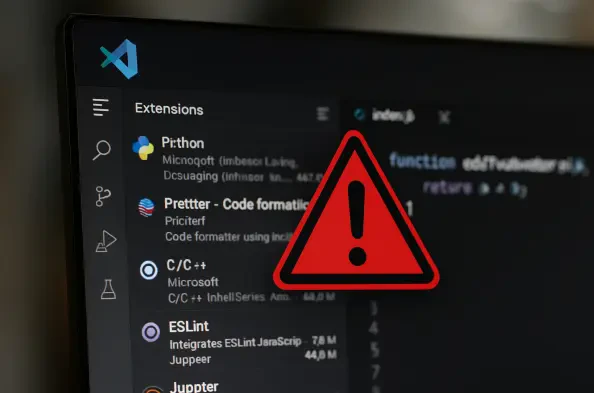
The very tools designed to streamline software development and enhance productivity have become a new battleground for cybercriminals, with the vast ecosystem of extensions for popular editors like Visual Studio Code emerging as a prime attack vector. A recent cybersecurity report has brought to light a targeted malware campaign that leverages the
In a world racing toward massive, cloud-based AI, data protection expert Vernon Yai champions a different path—one built on resilience, privacy, and precision. With a deep background in risk management and data governance, he argues that the future of enterprise AI lies not in a single, all-knowing oracle, but in a distributed network of small,
A security operations center receives an alert not from a suspicious external IP address but from its own security information and event management tool, the very system meant to be the first line of defense; this isn't a malfunction but a calculated takeover, a stark illustration of a tactical evolution in cybercrime where an organization's most
The Unseen Frontline: Why Your Web Browser Is Cybersecurity's New High-Stakes Target In a strategic move signaling a major shift in enterprise defense, cybersecurity giant CrowdStrike announced its planned acquisition of Seraphic Security, a pioneering browser security startup. This decision is far more than a simple corporate transaction; it's a
The deafening buzz of generative AI experimentation that defined the corporate landscape has given way to a stark and sober silence in boardrooms, replaced by a single, insistent question directed at the Chief Information Officer: What is the return on our investment? The grace period for exploration, a time of boundless pilot programs and