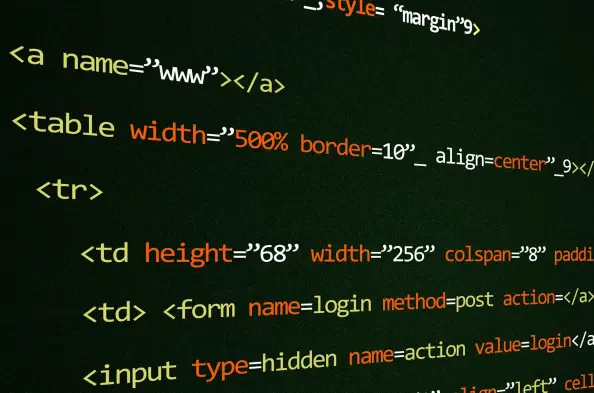
Data Minimization Techniques
The successful integration of Artificial Intelligence into mission-critical mainframe environments hinges less on the technology itself and more on the people behind the terminal, a reality that is becoming increasingly clear as organizations push forward with modernization. Much like learning to drive a car, theoretical knowledge of AI is not
Beneath the polished user interfaces and ambitious product roadmaps of many modern enterprises lies a silent saboteur that quietly erodes profitability and stifles innovation. This guide provides a strategic framework for executive leaders to diagnose, measure, and address the hidden risks of poor code quality. By moving this topic from the
In an era where digital information is a prime target for anonymous criminals, the legal system often struggles to keep pace, leaving companies and their users vulnerable when vast quantities of personal data suddenly appear for sale in the shadowy corners of the dark web. This digital reality was confronted head-on in a groundbreaking case where
The seemingly innocuous act of browsing the web now generates a cascade of data points, creating a detailed digital profile that is tracked, sold, and analyzed by corporations and monitored by agencies with alarming efficiency. In this landscape, the Virtual Private Network (VPN) has evolved from a tool for tech enthusiasts into a mainstream
Your personal information is being bought and sold every single day in a sprawling, largely unregulated digital marketplace, creating detailed profiles that can be used for everything from targeted advertising to identity theft. In this environment, where privacy laws like the GDPR and the California Consumer Privacy Act are racing to catch up