Endpoint Security
The rapid proliferation of artificial intelligence throughout modern enterprises has fundamentally reshaped business operations, but it has also quietly opened a new, unprotected frontier for cyberattacks. As organizations leverage everything from generative AI tools for employee productivity to sophisticated autonomous AI agents for complex
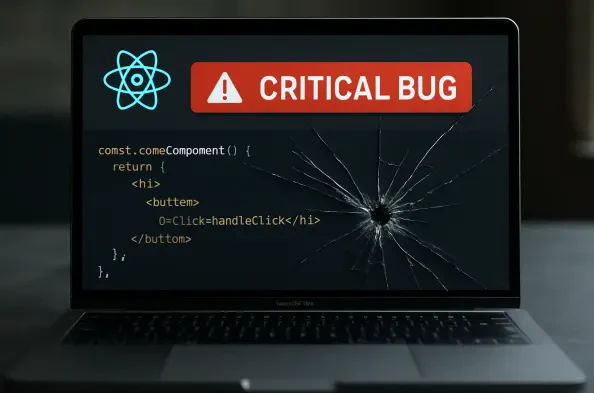
A recently disclosed vulnerability, so severe it fundamentally undermines the security of countless modern web applications, serves as a stark reminder that even the most trusted technologies can harbor catastrophic flaws. This maximum-severity vulnerability, codenamed React2shell and officially tracked as CVE-2025-55182, carries a perfect CVSS
The widespread, unsanctioned use of artificial intelligence tools by employees, a phenomenon known as "Shadow AI," is often misdiagnosed as a simple security failure or compliance breach. In reality, it represents a profound signal that employee workflows, productivity, and innovation are evolving at a pace that far outstrips the capacity of
A recently disclosed zero-day vulnerability actively exploited in the wild is posing a significant and immediate threat to Windows systems worldwide, targeting a core component responsible for cloud file integration. Identified as CVE-2025-62221, this critical flaw resides within the Windows Cloud Files Mini Filter Driver and creates a dangerous
A formidable new threat has emerged from the shadowy corners of Russian underground forums, rapidly becoming the weapon of choice for some of the most notorious ransomware gangs operating today. Known as Shanya, or alternatively VX Crypt, this sophisticated "packer-as-a-service" platform provides cybercriminals with a turnkey solution to cloak