Cloud Security
While the tech world fixated on the public debuts of large language models, a parallel revolution in cloud infrastructure quietly amassed a staggering 205% year-over-year growth, reshaping the very foundation of artificial intelligence development. This explosion gave rise to a new class of specialized providers, dubbed "neoclouds," which have
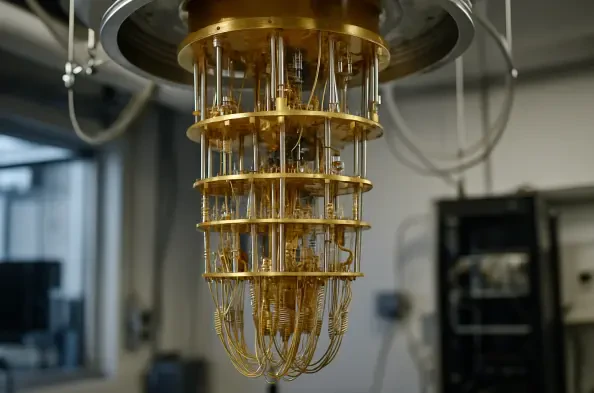
The year 2025 has firmly established itself as a critical inflection point for quantum technology, a period where a convergence of hardware innovations has begun to close the gap between theoretical potential and tangible, real-world utility. Across the globe, an accelerated pace of development within corporate labs, academic institutions, and
The Inevitable Collision of Cloud and Code The digital landscape is undergoing a seismic shift, driven by the relentless march of Artificial Intelligence, a transformation that is not merely incremental but a fundamental redefinition of how technology is built, deployed, and secured. As organizations race to integrate AI into every facet of their
With a sharp focus on risk management and the development of innovative detection techniques, Vernon Yai has established himself as a leading expert in data protection and privacy. We sat down with him to discuss a concerning surge in phishing attacks that cleverly exploit email routing misconfigurations to impersonate internal communications. He
The foundational trust in collaborative software development, particularly within open-source registries, is increasingly being weaponized by sophisticated threat actors who exploit these ecosystems for malicious distribution. This review explores NodeCordRAT, a potent remote access trojan that leverages the npm package registry as its primary