Risk Management
As AI reshapes the enterprise landscape, no role is undergoing a more profound transformation than that of the CIO. Vernon Yai, a leading expert in data protection and privacy governance, joins us to dissect this evolution. With a deep focus on risk management and safeguarding sensitive information, he offers a unique perspective on the challenges
Setting the Stage for a New Market Dynamic Imagine a world where the fiercest tech giants, once locked in bitter rivalry, now join forces to reshape the very foundation of enterprise IT. In 2025, this is no longer a distant vision but a tangible reality in the cloud computing arena. Major players like Amazon Web Services (AWS), Google Cloud, and
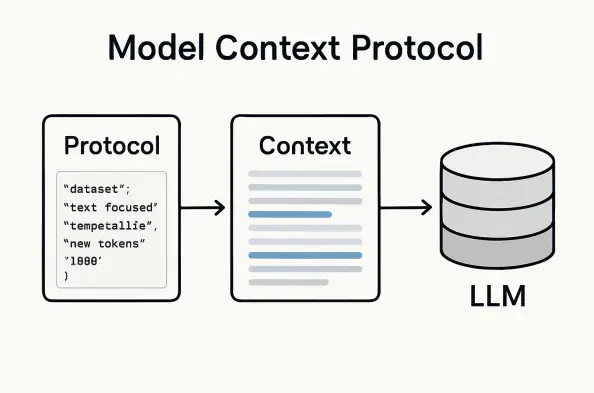
Imagine a world where connecting artificial intelligence assistants to vast arrays of external data and tools is as easy as plugging in a USB drive, yet the very simplicity that makes this possible also opens the door to a labyrinth of risks and roadblocks. This is the reality of Model Context Protocol (MCP) servers, a technology celebrated for
Imagine a world where the most precious resource isn’t gold or oil, but data—a digital treasure trove that holds the key to every decision, innovation, and strategy. In this realm, breaches and misuse loom like dark forces, threatening to unravel entire organizations. Who stands guard over this invaluable asset? Enter data stewards, the unsung
Vernon Yai has spent decades at the forefront of data analytics and financial management, specializing in transforming raw metrics into actionable strategies for enterprise success. As a seasoned expert in accounts receivable processes, Vernon has guided numerous firms through the intricate evolution of financial metrics, turning static reports